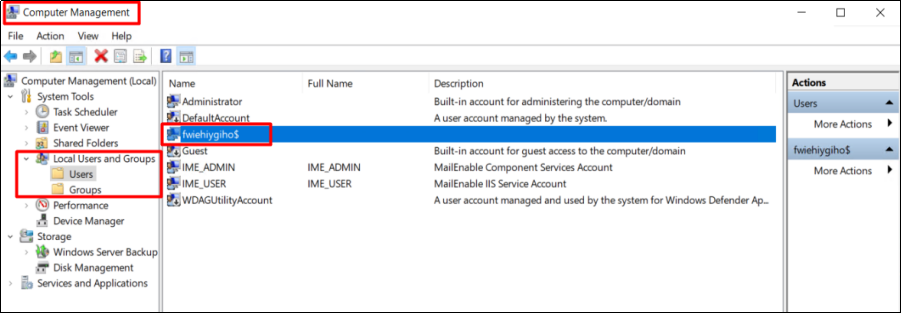
1 Check for hidden users or abnormal users
Open Computer Management -> Local Users and Groups. Check the name of the user/user group.
If the name contains a special symbol, such as $ or gibberish, it indicates that the user/user group is hidden and vulnerable to hacking.
If there are abnormal users or groups, please delete them.
2 Check abnormal processes
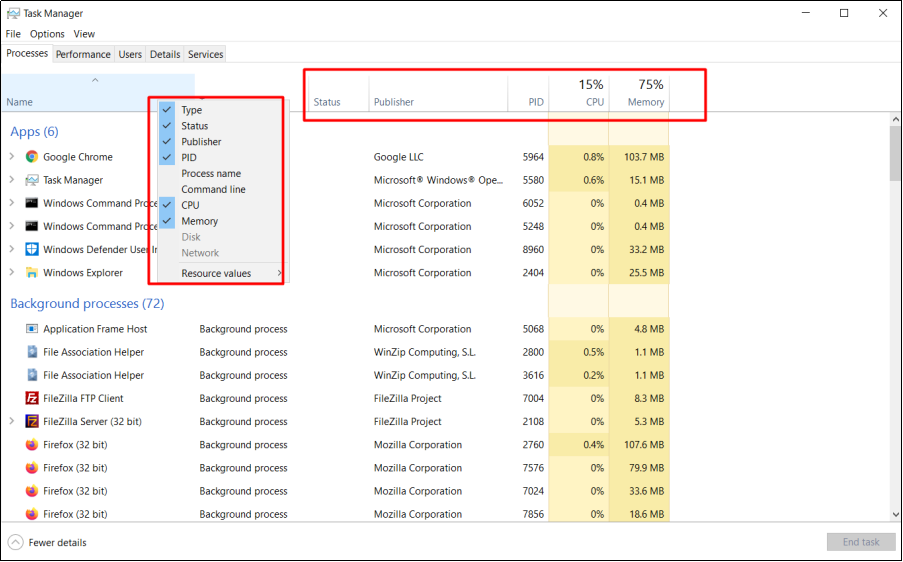
2.1 Check processes with high CPU and memory usageAbnormal processes may cause high CPU or memory usage. The Xmrig.exe process, as the screenshot shows, might be uploaded by a hacker.
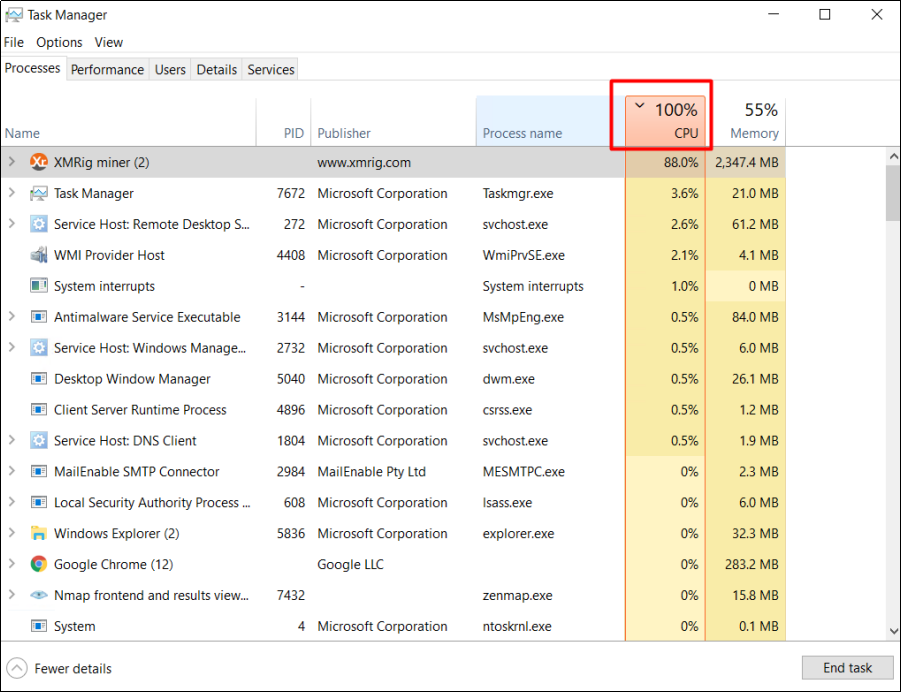
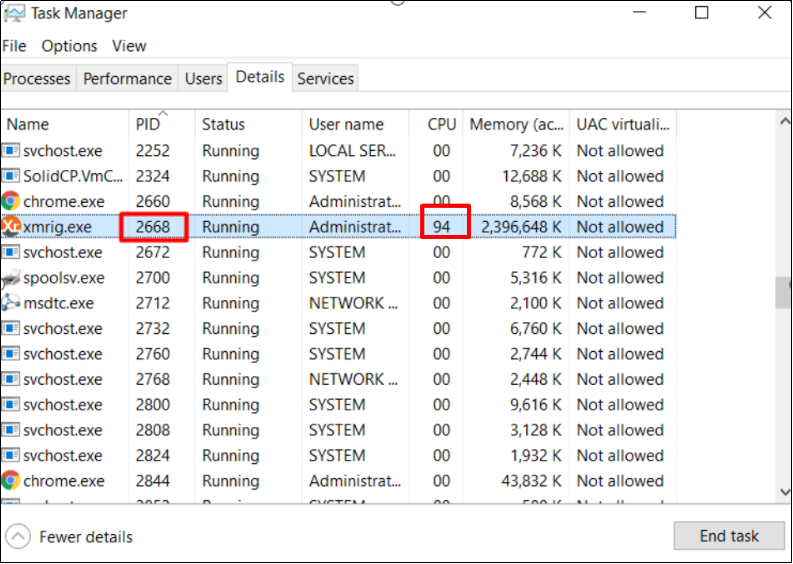
Right-click on the top menu to find out the name of the application publisher as highlighted below.
Notice any suspicious processes and carry out further investigations. The following shows how to enable the menu of Type, Status, Publisher, PID, and so on.
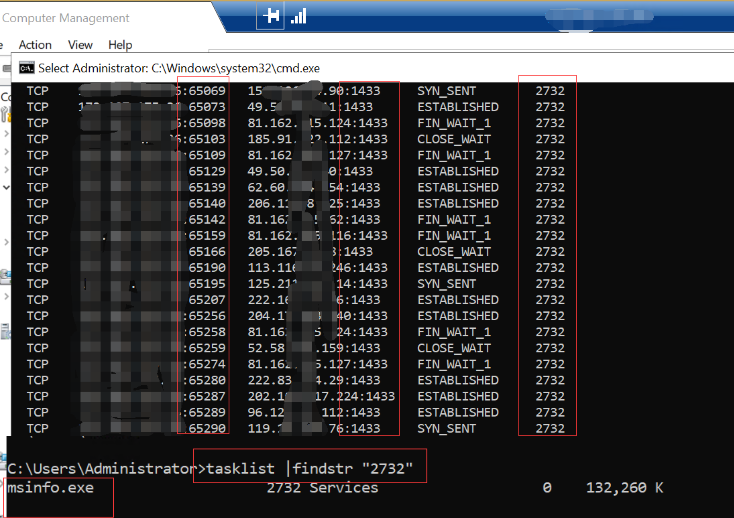
Open the command prompt on your PC and type “netstat -ano” to check all connections.
If there are many connections from the same PID, please enter command tasklist |findstr “pid” to check the related services that use the PID.
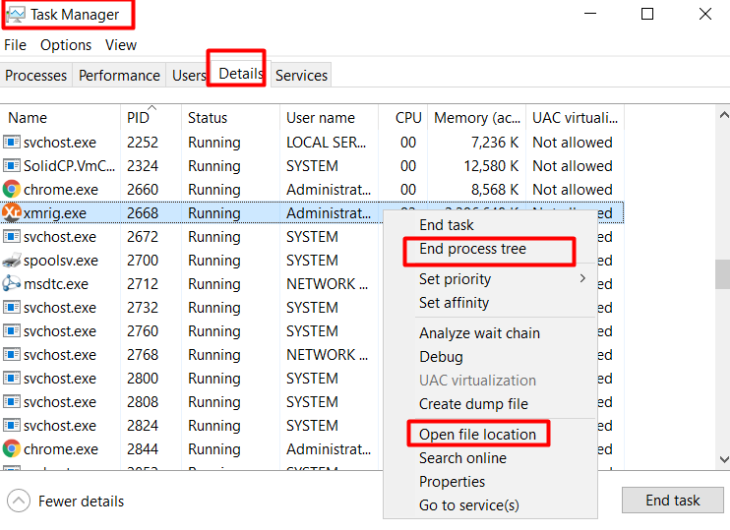
If you identify a malicious process, right-click on the process name and click “End Process Tree”. Choose “Open file location” to delete the abnormal files.
This disconnects your server from the suspicious connections and all its dependencies. The following shows how to end a process.
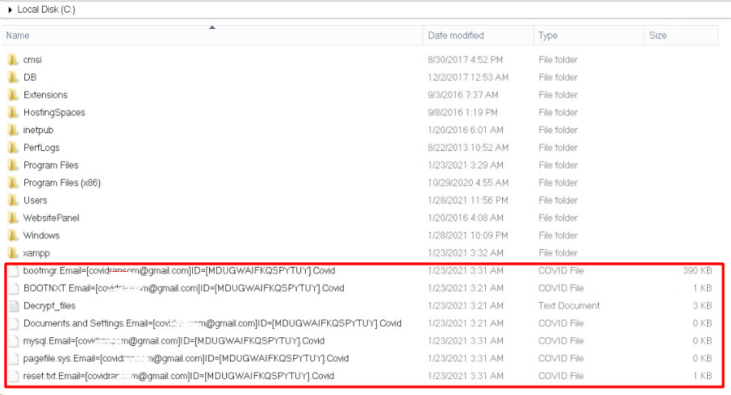
3 Check Windows system directories
Check the system directories in Windows such as “C:Windows” and “C:WindowsSystem32”. If there are abnormal scripts or executable files in your server as the screenshot shows, your server probably has been hacked.
4 Check firewall rules
Check whether there are garbled firewall rules or strange ports opened. If there are abnormal firewall rules, please delete them. An example of abnormal firewall rules is shown below.
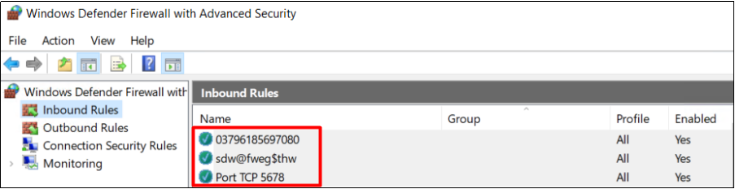
5 Check tasks in Task Scheduler
Go to the start menu, enter "task scheduler" and open it. Check if there are abnormal tasks listed in the library. If there are abnormal tasks, please disable and delete them. The following shows how to disable and delete a task.
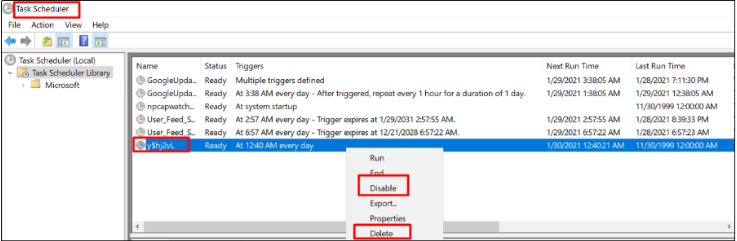
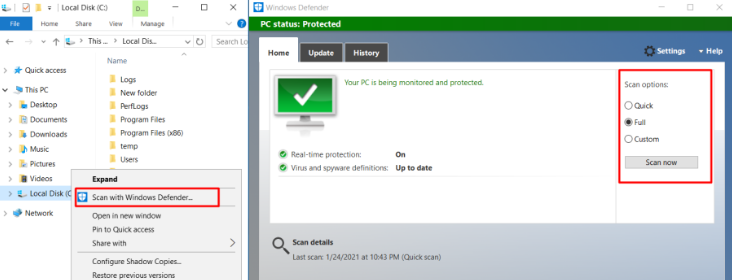
6 Scan all drives through Windows Defender
If the server is based on Windows Server 2016/2019, clients can use Windows Defender to scan the server. If the server is based on Windows Server 2008/2012 R2, you can install Microsoft Security Essentials. Other security software is available too.
Click Clean up if any suspicious files are found after scanning.