Introduction
To increase the security level of the host, openssh can disable users from logging in with password-based authentication. Instead, key-based authentication is used.
1. Change two options in the configuration file.
-
Disable SSH password authentication.
-
Restrict root from logging in remotely.
Run the command "vi /etc/ssh/sshd_config" and ensure these lines:
PasswordAuthentication yes
PermitRootLogin yeslook like this:
PasswordAuthentication no
PermitRootLogin no2. Restart the SSH service to enable your changes.
Note that it is a good idea to have two active connections to your server before restarting the SSH server. Having that extra connection allows you to fix anything should the restart go wrong.
$ sudo service sshd restartNow, you can't log in to the remote host using password.
3. Add users and assign keys
Suppose, you are the system administrator.
Now you need to add a user to the system who can connect remotely to use the system, and the new user has the following attributes:
-
User name: stu
-
User home directory: /home/stu
-
Authentication method: key authentication
3.1. Use "useradd" command to add user
[root@centos ~]# useradd stu
3.2. Use su command to switch to new user.
[root@centos ~]# su - stu
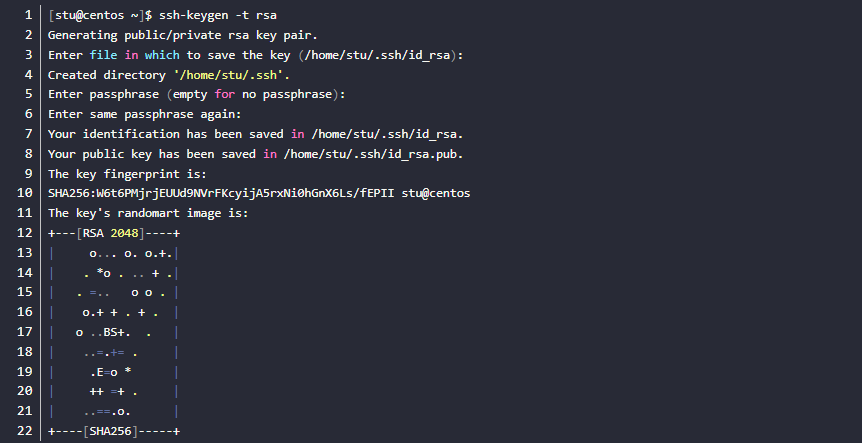
3.3 Use ssh-keygen -t rsa to generate a public-private key pair (all options are default)
4. Configure and modify the public key file authorized_keys
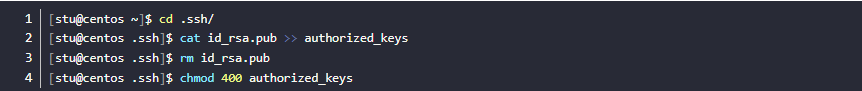
Enter the .ssh directory of the stu user's home directory.
append the public key to the public key file authorized_keys specified by the stu user.
delete the original public key file in time after completion, and change the permission of authorized_keys to 400, that is, only the owner stu can read.
5. Send key file to client
Finally, send the private key file to the user via a secure method (such as email). After the user gets the private key, he can log in to the host using a client with SSH using key authentication.


